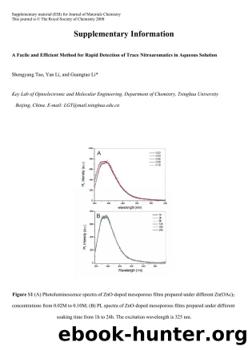
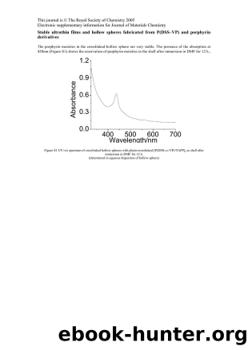
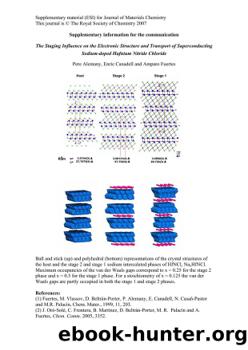
Certification
pdf | | 2016-10-27 | Author:unknow
( Category:
Security
December 4,2024 )
pdf | | 2024-10-24 | Author:Jeanne Boyarsky & Scott Selikoff [Boyarsky, Jeanne & Selikoff, Scott]
( Category:
Oracle
November 24,2024 )
pdf | | 2023-11-20 | Author:Mike Chapple & David Seidl [Mike Chapple]
( Category:
CompTIA
November 19,2024 )
pdf | | 2024-09-30 | Author:Robert Shimonski & Martin Weiss [Robert Shimonski]
( Category:
CompTIA
November 19,2024 )
epub |eng | 2025-11-15 | Author:Dayne Sorvisto
( Category:
Microsoft
November 8,2024 )
pdf | | | Author:Compaq_Owner
( Category:
Microsoft
October 25,2024 )
pdf | | | Author:Unknown
( Category:
Microsoft
October 20,2024 )
pdf | | 2007-09-25 | Author:Unknown
( Category:
Microsoft
October 18,2024 )
pdf | | 2007-09-05 | Author:Mike Brook
( Category:
Microsoft
October 10,2024 )
pdf | | 2009-09-08 | Author:martinc
( Category:
Microsoft
October 10,2024 )
pdf | | 0101-01-01 | Author:withersn
( Category:
Microsoft
October 10,2024 )
pdf | | 2008-07-17 | Author:martinc
( Category:
Microsoft
October 10,2024 )
pdf | | 0101-01-01 | Author:withersn
( Category:
Microsoft
October 10,2024 )
pdf | | 2007-09-27 | Author:martinc
( Category:
Microsoft
October 10,2024 )
Popular ebooks
OCA Java SE 8 Programmer I Certification Guide by Mala Gupta(9796)Red Hat Certified Specialist in Services Management and Automation EX358 Exam Guide by Eric McLeroy(6178)
The KCNA Book by Nigel Poulton(4250)
Microsoft Security, Compliance, and Identity Fundamentals Exam Ref SC-900 by Dwayne Natwick(3617)
Designing and Implementing Microsoft Azure Networking Solutions by David Okeyode(3525)
Microsoft Security Operations Analyst Exam Ref SC-200 Certification Guide by Trevor Stuart and Joe Anich(3474)
Microsoft Security Operations Analyst Exam Ref SC-200 Certification Guide by Trevor Stuart & Joe Anich(3397)
TCP IP by Todd Lammle(2983)
Microsoft Power BI Data Analyst Certification Guide by Ed Corcoran Orrin Edenfield(2921)
Unity Certified Programmer: Exam Guide by Philip Walker(2573)
MCSA Windows Server 2016 Study Guide: Exam 70-740 by William Panek(2520)
Networking A Beginner's Guide by Bruce Hallberg(2210)
Microsoft Power Platform Solution Architect's Handbook by Hugo Herrera(2037)
31 Days Before Your CompTIA A+ Exams (Shanette Luellen's Library) by Benjamin Patrick Conry(1861)
CompTIA A+ Practice Tests Core 1 (220-1101) and Core 2 (220-1102) by Ian Neil and Mark Birch(1794)
MCSA Windows Server 2016 Study Guide: Exam 70-741 by William Panek(1666)
PHP 7 Zend Certification Study Guide by Andrew Beak(1645)
Healthcare Information Security and Privacy (All-In-One) by Sean Murphy(1551)
CompTIA A+ Certification Guide (220-901 and 220-902) by Matthew Bennett(1526)
RHCSA & RHCE Red Hat Enterprise Linux 7: Training and Exam Preparation Guide (EX200 and EX300), Third Edition by Asghar Ghori(1488)