Computers & Technology
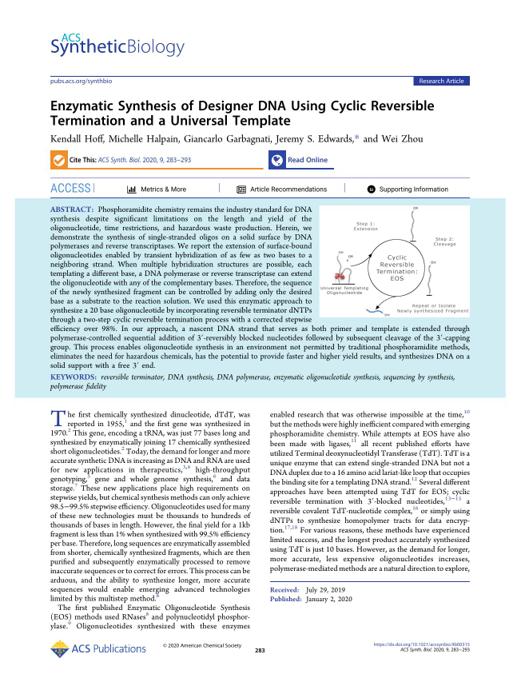
pdf | | 2020-02-14 | Author:Kendall Hoff, Michelle Halpain, Giancarlo Garbagnati, Jeremy S. Edwards, and Wei Zhou
( Category:
Algorithms
February 11,2023 )
pdf | | 2020-09-10 | Author:Jingjing Deng, Jakob H. Viel, Jingqi Chen, and Oscar P. Kuipers
( Category:
Computer Simulation
February 11,2023 )
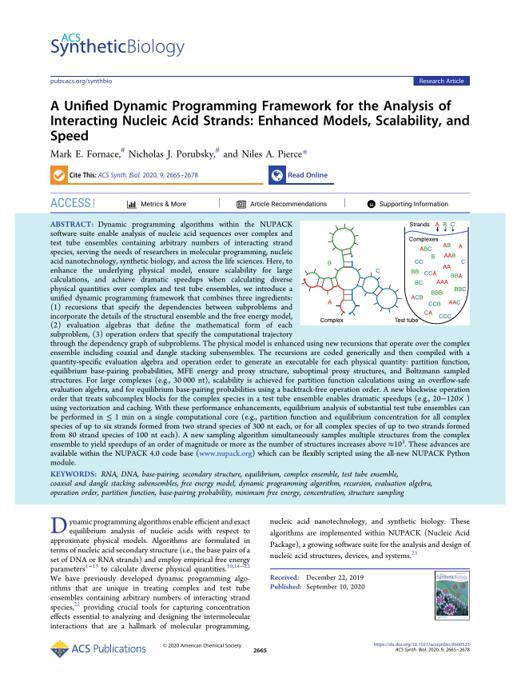
pdf | | 2020-10-08 | Author:Mark E. Fornace, Nicholas J. Porubsky, and Niles A. Pierce
( Category:
C & C++
February 11,2023 )
epub |eng | 2023-01-20 | Author:MAXWELL FLITTON
By the end of this chapter, we will have refactored our Rust application to support the principles of RESTful APIs. This means that we are going to map out the ...
( Category:
Programming
February 10,2023 )
epub |eng | 2023-01-13 | Author:Marco Castorina | Gabriel Sassone
We have to populate a VkPipelineRenderingCreateInfoKHR structure with the number of attachments we are going to use and their format. We also need to specify the depth and stencil formats, ...
( Category:
Rendering & Ray Tracing
February 10,2023 )
pdf | | | Author:Unknown
( Category:
Mathematical & Statistical
February 10,2023 )
pdf | | 2010-01-29 | Author:Richard M. Heiberger, Erich Neuwirth
( Category:
Mathematical & Statistical
February 10,2023 )
pdf | | 2007-10-18 | Author:Unknown
( Category:
C++
February 10,2023 )
epub, pdf |eng | 2022-08-16 | Author:George Bokhua [George Bokhua]
Logo for the ACT research center; Created by a chain of accidents This is not work to present to a client; nor is it advised to make such work public. ...
( Category:
Architecture
February 10,2023 )
pdf | | 2005-04-26 | Author:SEARCH ENGINE OPTIMIZATION(2007)
( Category:
Search Engine Optimization
February 10,2023 )
azw3 |eng | 2022-11-08 | Author:David Anderson [Anderson, David]
*Remember, just because you can, doesnât mean you should. Always invest in technical leadership: it should be clear to stakeholders why things are happening. If a technical lead makes you ...
( Category:
Accounting
February 9,2023 )
epub |eng | 2022-12-21 | Author:Bruce Schneier
38 The Context of a Hack What I am developing is a sophisticated notion of hacking. Itâs not that hacks are necessarily evil. Itâs not even that theyâre undesirable and ...
( Category:
Architecture
February 9,2023 )
pdf |en | | Author: Cheryl A. Schmidt & Christopher Lee
( Category:
CompTIA
February 9,2023 )
pdf |en | | Author: Gonzalo Navarro
( Category:
Structured Design
February 9,2023 )
mobi, epub |eng | 2022-09-15 | Author:Michael Hartl
( Category:
JavaScript
February 9,2023 )
Categories
Popular ebooks
Deep Learning with Python by François Chollet(24176)The Mikado Method by Ola Ellnestam Daniel Brolund(21442)
Hello! Python by Anthony Briggs(20697)
Secrets of the JavaScript Ninja by John Resig Bear Bibeault(19130)
Dependency Injection in .NET by Mark Seemann(18771)
The Well-Grounded Java Developer by Benjamin J. Evans Martijn Verburg(18369)
Kotlin in Action by Dmitry Jemerov(18123)
OCA Java SE 8 Programmer I Certification Guide by Mala Gupta(18025)
Adobe Camera Raw For Digital Photographers Only by Rob Sheppard(16942)
Algorithms of the Intelligent Web by Haralambos Marmanis;Dmitry Babenko(16863)
Grails in Action by Glen Smith Peter Ledbrook(16000)
Sass and Compass in Action by Wynn Netherland Nathan Weizenbaum Chris Eppstein Brandon Mathis(13718)
Secrets of the JavaScript Ninja by John Resig & Bear Bibeault(11736)
Test-Driven iOS Development with Swift 4 by Dominik Hauser(10601)
A Developer's Guide to Building Resilient Cloud Applications with Azure by Hamida Rebai Trabelsi(10583)
Jquery UI in Action : Master the concepts Of Jquery UI: A Step By Step Approach by ANMOL GOYAL(9669)
Hit Refresh by Satya Nadella(9096)
The Kubernetes Operator Framework Book by Michael Dame(8530)
Exploring Deepfakes by Bryan Lyon and Matt Tora(8355)
Robo-Advisor with Python by Aki Ranin(8299)